Understanding Single Sign-On (SSO)
Single sign-on is a one-time user authentication solution that enables users to log in to multiple programs and websites. Organizations prioritize access management methods that enhance security and the user experience since customers often access applications directly from their browsers today. SSO offers both aspects, as users can access all password-protected resources without repeating logins once their identity has been verified.
SSO is a crucial aspect of Identity and Access Management (IAM). Proper SSO solution implementation within an organization simplifies overall password management, improving productivity and security and lowering the risk of forgotten, weak, or lost passwords.
How does SSO work?
The identity provider delivers the required credentials to the service provider after the user has been authenticated, allowing the user to access the requested resource. Users no longer need to keep track of and maintain numerous usernames and passwords, simplifying the login process and enhancing the user experience.
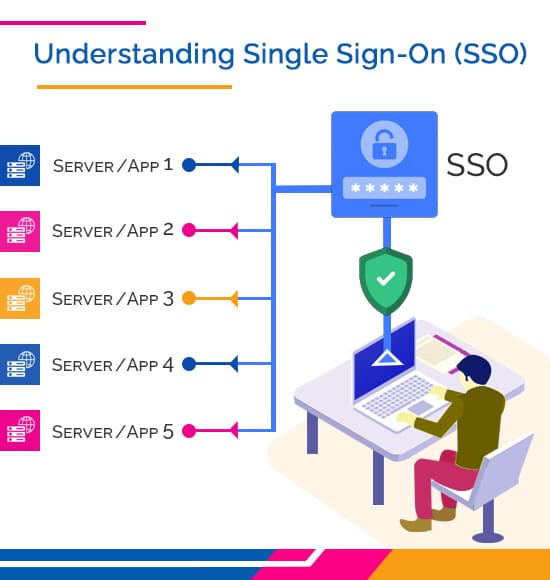
SSO works by first verifying a user’s identity and then granting access to any applications and services the user is authorized to use. The SSO system requests identity verification from the user’s identity provider whenever a user attempts to access a resource from a service provider. This is accomplished by the application and a centralized SSO service completing a series of authentication, validation, and communication procedures. The critical elements of SSO solutions are shown below.
SSO Service
An SSO service is a centralized authentication system on which applications rely during user login. When an unauthenticated user attempts to access an application, the application directs them to the SSO service. The SSO service then validates the user’s identity and redirects them to the initial application. Typically, this service runs on a dedicated SSO policy server.
SSO Token
An SSO token is a digital file containing user-identifiable details, such as a username or email address. When a user seeks access to an application, the application verifies the user by exchanging an SSO token with the SSO service.
What are the types of SSO?
SSO solutions incorporate various standards and protocols to verify and authenticate user credentials.
OAuth
Open Authorization or OAuth is an open-standard authorization system that allows “secure designated access” for applications. For instance, you can allow Facebook to view your profile or post updates to your timeline without revealing your Facebook password to ESPN. This significantly reduces danger since even if ESPN experiences a breach, your Facebook password is secure.
SAML
Security Assertion Markup Language (SAML) is an open federation standard that enables an identity provider (IdP) to authenticate users and then provide an authentication token to a different application known as a service provider (SP). SAML facilitates SP to function without having to perform its authentication or pass the identity to integrate internal and external users.
It enables the network, typically an application or service, to share security credentials with an SP. In addition to a limited number of other identity management systems installed on-site or in a different cloud, SAML enables safe, cross-domain communication between the public cloud and other SAML-enabled systems. Using SAML, you can provide your users with a single sign-on (SSO) experience across any two apps that support the SAML protocol and services. This enables an SSO to perform various security tasks for one or more applications.
OIDC
OpenID allows users to access multiple sites using a single set of credentials. It enables the service provider to assume the duties of user credential authentication. Web applications leverage OIDC to make additional requests and verify the user’s authenticity rather than sending an authentication token to a third-party identity service.
Kerberos
Kerberos is a ticket-based authentication system that enables two or more parties to mutually authenticate their identity on the network. It employs security cryptography to prevent unauthorized access to identity information exchanged between the server, clients, and Key Distribution Center.
Advantages of SSO
Users and businesses benefit from using SSO to simplify user logins in several ways.
It boosts employee and IT productivity
A single point of access, however, will cut down on wastage of both time and resources. How? Read on.
Single sign-on enables you to:
Reduce the frequency of support calls: Customers who only need one password to access all of their apps won’t need it as frequently.
Improve user experience: Users can save between 5 and 15 seconds per login, as there is no requirement to switch between numerous login URLs or reset passwords.
Reduce security risks: Employees are not endangering their safety by using their SSO login information on any device or web browser.
As you can see, single sign-on’s ability to increase end users’ productivity is one of its biggest benefits.
Enhance security capabilities
Users are more inclined to create a stronger (harder to guess) passphrase and are less likely to write it down because they only need to remember one password for different applications. These best practices decrease the risk of password theft.
It combines with Risk-Based Authentication (RBA)
You can combine SSO with risk-based authentication (RBA) for even more security. You and your security team can monitor user behavior with RBA. In this method, you can request additional identification verification if you see any unusual user behavior, including using an incorrect IP address or repeated login failures. You may restrict access if the user fails at this.
Reduce expenses
Enterprise customers risk losing their login information by remembering several passwords. The workload for the internal IT staff grows as a result of the frequent requests for password recovery or resets. Using SSO lessens the likelihood that passwords will be lost, which cuts down on the resources required to handle requests for password resets.
It prevents shadow IT
Shadow IT isn’t anything new in the cybersecurity industry. It refers to illegal downloads in the workplace.
Previously, only employees could use Shadow IT to buy software from office supply stores. But so far, as cloud-based downloads gain popularity, the risk factor increases.
IT administrators can utilize Single sign-on to monitor which apps users use to address this problem. As a result, the threat of identity theft can be avoided.
FAQs
Que-1: Does SSO require Active Directory?
Ans: So, the short answer to whether you require both AD and Single sign-on is no you do not require both AD and an SSO solution.
Que-2: Where is the SSO token stored?
Ans: SSO presents the user with a login form, validates the user’s information, and issues a token. The token is stored in a cookie on SSO.
Que-3: Does SSO work outside my corporate firewall?
Ans: Yes. Users can sign into Salesforce with their network passwords outside the corporate firewall. Alternatively, you can make it mandatory for users to join your company’s network before logging in.
Que-4: Can I Use a Third-Party Identity Provider’s MFA Service for SSO?
Ans: Yes. You can centralize your SSO and MFA solutions by utilizing the MFA service provided by your third-party identity provider. It also provides MFA to external apps that integrate with the third-party identity provider. Furthermore, when users log in through your identity provider, they are granted high-assurance access and are not required to provide a verification method by Salesforce.